How Access Control Works
Access is granted through theaccess property on resources, which can be modified in your project’s suga.yaml or through the visual editor with the suga edit CLI command.
- IAM policies (AWS) with least-privilege permissions
- Service account bindings (GCP) with appropriate roles
- Network security rules allowing service-to-resource communication
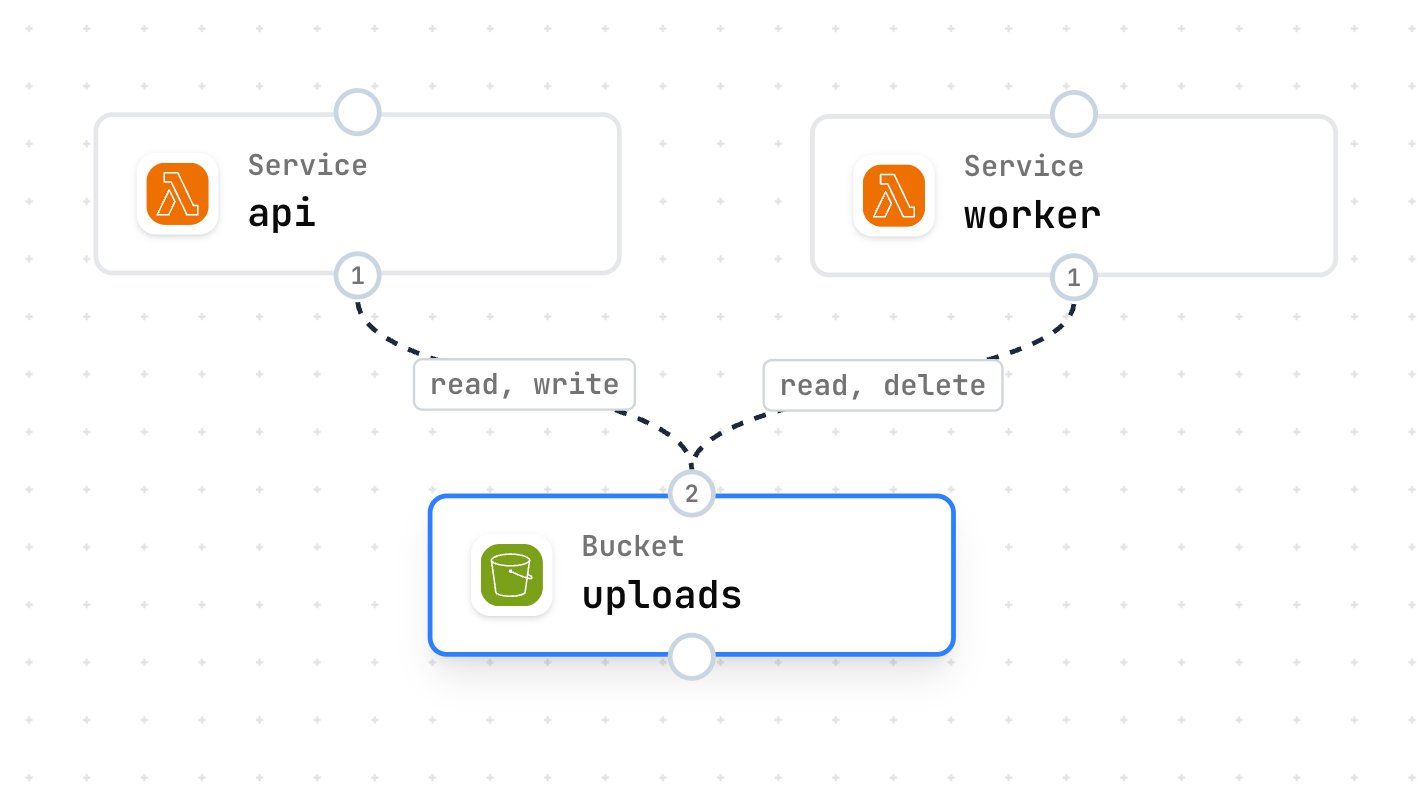
Permission Types
Bucket Permissions
read- Download/read objectswrite- Upload/write objectsdelete- Delete objectsall- Shorthand for read, write, delete
Database Permissions
query- Full SQL access (SELECT, INSERT, UPDATE, DELETE)
Least Privilege
Suga encourages and follows the principle of least privilege:- By default, services cannot access other resources
- Services only get permissions they need
- No wildcards or overly broad policies
- Separate identities per service
suga/aws), here is an example of the kind of IAM policy that will be generated:
If you use your own Suga resource plugins, you’re free to construct the IAM, roles, etc. as you see fit.
Best Practices
- Grant minimum permissions - Only what each service needs
- Separate services - Different services for different roles
- Review access patterns - Regularly audit who accesses what
- Use read-only when possible - Many services only need read access