Overview
Personal Access Tokens (PATs) are an alternative to using passwords for authentication to Suga when using the Suga CLI or API. Personal access tokens are intended to access Suga resources on your behalf. A token has similar capabilities to access resources and perform actions that you have as the token owner, with a few restrictions. You can use a personal access token to:- Authenticate the Suga CLI in CI/CD environments
- Make direct API calls to Suga services
- Automate workflows without interactive device authorization flow
- Manage tokens (create, revoke, or edit personal access tokens)
- Access the Suga Agent chat API (use the Suga CLI MCP server for AI-assisted development instead)
Creating a Personal Access Token
Personal access tokens will become inactive if you lose access to the resources they were created for, such as when you’re removed from a team or project.
Navigate to Settings
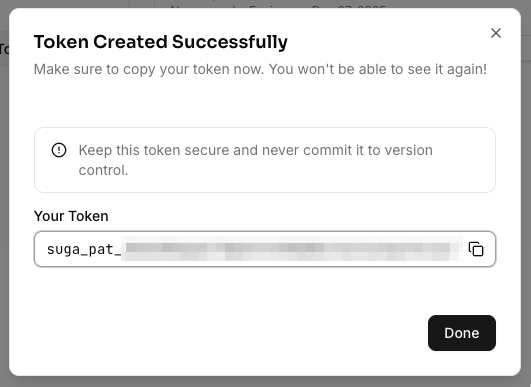
Log in to Suga and click the Settings link in the navigation menu, then click on Personal Access Tokens in the sidebar.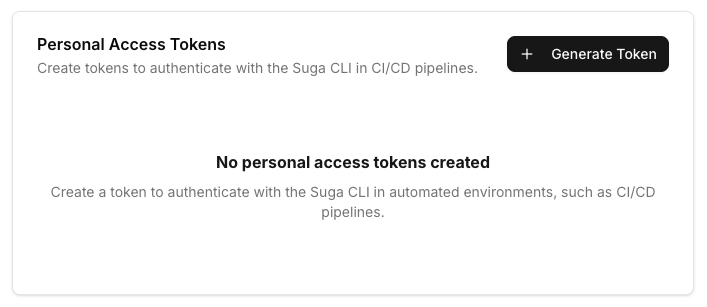

Configure Your Token
In the token creation modal, provide the following information:Token Name (required)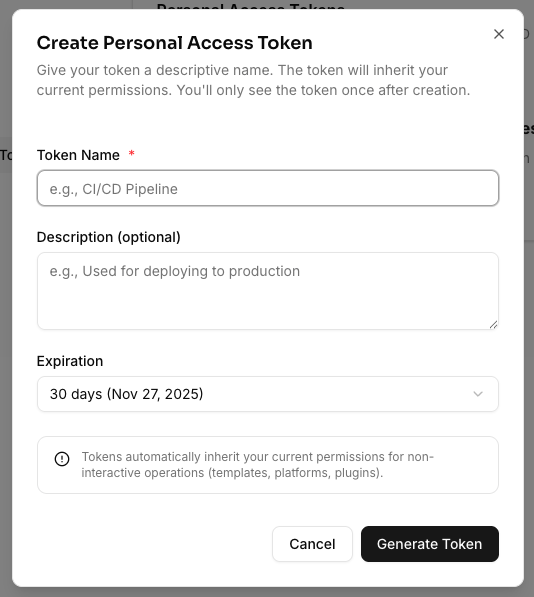
- A descriptive name to help you identify the token’s purpose
- Example: “GitHub Actions CI”, “Production Deploy”, “Local Development”
- 7 Days - Short-term tokens for temporary access or testing
- 30 Days - Standard tokens for most use cases
- 60 Days - Medium-term tokens for ongoing projects
- 90 Days - Long-term tokens for stable workflows
- Custom Date - Specify an exact expiration date
- No Expiration - Token never expires (not recommended)
- Additional context about the token’s purpose or usage
- Helps with token management and auditing

Token Security Best Practices
Personal access tokens are like passwords, and they share the same inherent security risks. Before creating a new personal access token, consider if there is a more secure method of authentication available to you:- To access Suga from the command line, you can use
suga loginwith the device authorization flow instead of creating a personal access token - When using a personal access token in a GitHub Actions workflow, consider storing your token as a secret. For more information, see CI/CD Authentication
Keeping your personal access tokens secure
When using a personal access token in a script, you can store your token as a secret and run your script through GitHub Actions or another CI/CD platform. You can also store your token in environment variables. For best practices:- Treat tokens like passwords - Never share tokens or commit them to version control
- Store tokens securely - Use environment variables or secret management services (like GitHub Secrets, AWS Secrets Manager, HashiCorp Vault)
- Use descriptive names - Make tokens easy to identify and manage
- Set appropriate expiration - Choose the shortest expiration that meets your needs
- Rotate regularly - Periodically regenerate tokens used in production, even before expiration
- Revoke unused tokens - Immediately delete tokens that are no longer needed
- Create separate tokens - Use different tokens for different purposes rather than reusing the same token everywhere
- Monitor token usage - Regularly review your active tokens and their last used timestamps in the Settings page
- Revoke on breach - If a token is compromised, revoke it immediately and investigate what resources may have been accessed
Managing Tokens
Viewing Active Tokens
In the Personal Access Tokens section, you can view:- Token names and descriptions
- Creation timestamps
- Expiration timestamps
- Last used timestamps
Revoking Tokens
To revoke a token:- Navigate to Settings > Personal Access Tokens
- Find the token you want to revoke
- Click the Delete button
- Confirm the revocation