Browse Platforms
Explore official and community platforms in the platform browser
What is a Platform?
A platform is a configuration that maps Suga’s abstract resource types (services, buckets, databases, entrypoints, etc.) to specific implementations. For example, the official Suga AWS platform maps:- Services → AWS Lambda or ECS Fargate
- Buckets → S3 buckets
- Entrypoints → Amazon CloudFront CDN
Platform Ecosystem
Official Platforms
The Suga team maintains official platforms for major cloud providers. These are general purpose, production-ready implementations:- AWS Platform - Lambda/Fargate services, S3 storage, CloudFront CDN, IAM security
- GCP Platform - Cloud Run services, Cloud Storage, Cloud CDN, Service Account security
- Azure Platform (coming soon) - Container Apps services, Blob Storage, etc.
Example: Using official platforms
Community Platforms
The platform ecosystem extends far beyond official implementations. Community members and organizations are able to publish platforms for:- Alternative cloud providers - Azure, DigitalOcean, Linode, Vultr
- Specialized deployments - Kubernetes, Docker Swarm, on-premises infrastructure
- Development environments - Local testing, CI/CD pipelines, staging environments
- Custom configurations - Organization-specific security policies, compliance requirements
Platform names follow the format
team/platform@version (e.g. acme-corp/azure@2).You can discover available platforms through the Suga platform registry or by browsing community repositories.Platform Components
Platforms operate through two key mechanisms: Infrastructure Generation and Runtime Adaptation.Infrastructure Generation
When you runsuga build, Suga uses your target platform to transform your Project specification into cloud-specific Terraform HCL (called stacks). This process:
- Maps abstract resources - Takes your high-level resource definitions (services, buckets, databases) and selects appropriate cloud implementations
- Generates Terraform modules - Creates infrastructure-as-code that provisions actual cloud resources with proper networking, security, and permissions
- Applies platform policies - Ensures generated infrastructure follows organizational security, compliance, and architectural standards
Runtime Adaptation
If you choose to use Suga’s client code generation in your applications, Platforms provide runtime adapters that translate those abstract operations into cloud-specific API calls:Resource Blueprints
Ultimately, Suga Platforms map Suga Resources to specific plugins and configuration, called Resource Blueprints. Blueprints specify:- Plugin: The resource plugin to use, which contains Terraform code and optional Runtime Adapter
- Properties: Configuration for the plugin, typically Terraform Module variables
- Variables: Custom values to export as Terraform stack variables
- Dependencies: Other infrastructure that should be deployed before the current resource
Plugins
Platforms use a modular plugin system where each plugin handles a specific cloud service:suga/aws-lambda- AWS Lambda functionssuga/aws-s3-bucket- S3 storage bucketssuga/gcp-cloudrun- Google Cloud Run containerssuga/neon-db- Neon PostgreSQL databases
Properties
Properties are key-value pairs that get passed directly as input variables to the underlying Terraform modules. They configure how the cloud resources should be deployed and behave. The visual editor provides an intuitive interface for editing blueprint properties: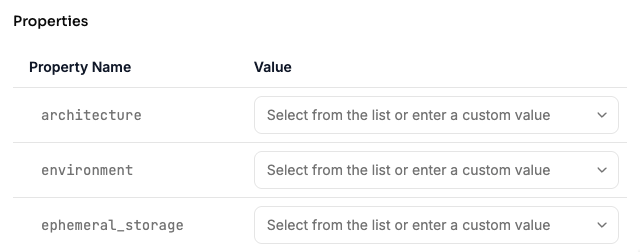
Platform blueprint with properties
- Static values - Strings, numbers, booleans, objects, and arrays
- Variable references -
${var.domain}references platform variables - Self references -
${self.waf_enabled}references blueprint-specific variables - Infrastructure references -
${infra.vpc.id}references other infrastructure outputs
Generated Terraform module call
Variables
Variables provide a way to defer configuration values until deployment time, making platforms flexible and reusable. Suga supports two types of variables that become Terraform stack variables:Platform Variables
Platform variables are defined at the top level and can be referenced by any blueprint in the platform: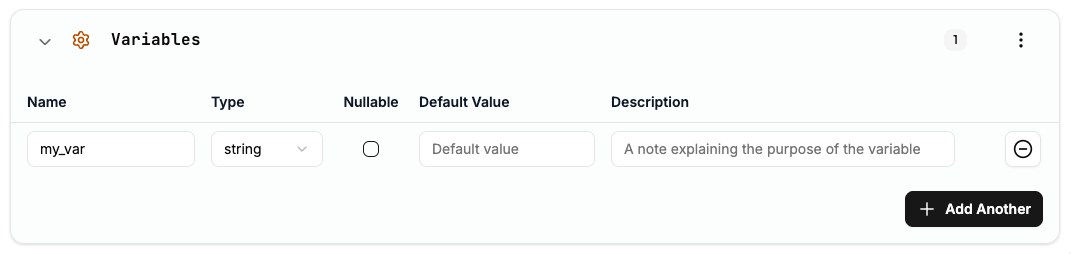
Blueprint Variables
Blueprint variables are specific to individual resource blueprints, allowing fine-grained customization. The visual editor shows how blueprint variables can be used as property values: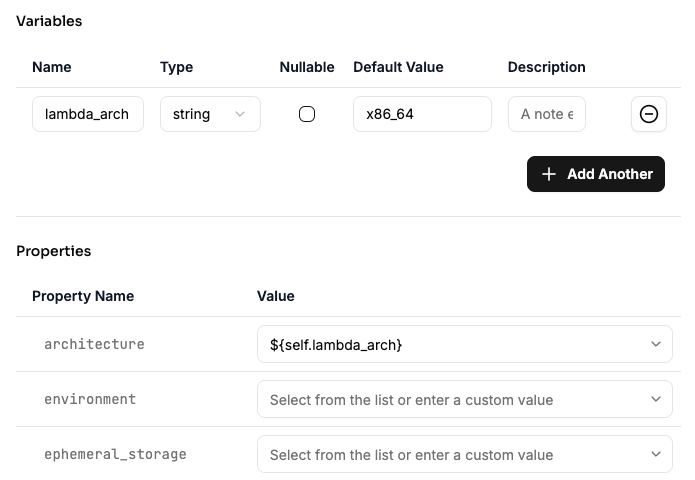
Variable Resolution
When you runsuga build, variables become Terraform stack variables that can be provided at deployment time:
Conceptual Example of Stack Variables
Providing variables at deploy time
Multi-Environment Deployments
Variables work seamlessly with Terraform workspaces to support deployment to multiple environments using different configurations:Environment-specific deployments
environments/dev.tfvars
environments/prod.tfvars